Simplified USB Security Hardware
Introducing the Skeleton Key: A groundbreaking innovation, powered by Xorre OS, designed to bring cyber conflict tools to the hands of ideologically aligned civilian groups. We recognize that while many are willing to participate in this new form of conflict, the technical skills required often pose a significant hurdle.
With Skeleton Key and Dissident, we aim to bridge this gap. Our platform is built with simplicity at its core, providing a user-friendly experience even for those with no technical skills. Through single-button interfaces, we make cyber operations as easy as counting 1,2,3,4, enabling anyone, anywhere in the world, to participate meaningfully in cyber conflict.
Tools ANYBODY
can use

At the heart of Xorre OS lies a custom GUI and interface that transforms complex technical functions into a format accessible to all. Built on the robust foundations of Qubes OS – the “reasonably secure Operating System” famously used by Edward Snowden – our platform ensures a secure environment for users.
The 4-button interface, requiring no technical interaction or configuration, is universally comprehensible, transcending language and cultural barriers. With Xorre OS, we simplify cyber operations, making them readily accessible to all willing participants, regardless of their technical expertise.
As your skills grow, discover a suite of advanced security tools with Xorre’s simplified control schemes, providing direct access to pre-configured offensive security containers. The modular nature of these containers allows an infinite combination of tools that can be stacked in diverse configurations, providing a flexible and powerful solution for cyber security operations.

Built for non-technical populations
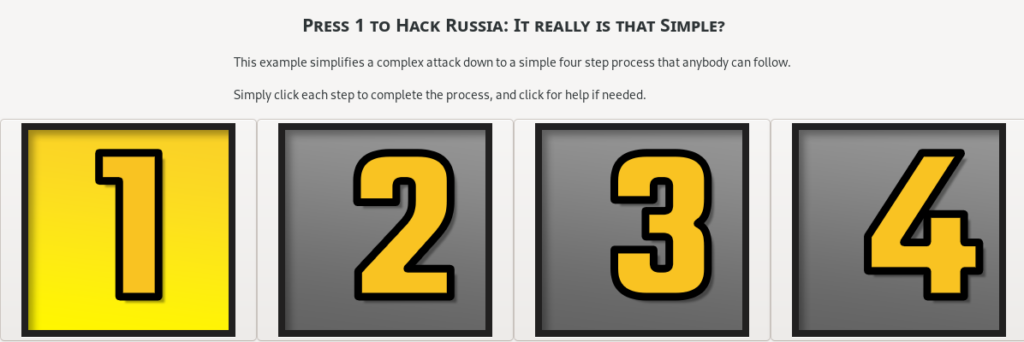
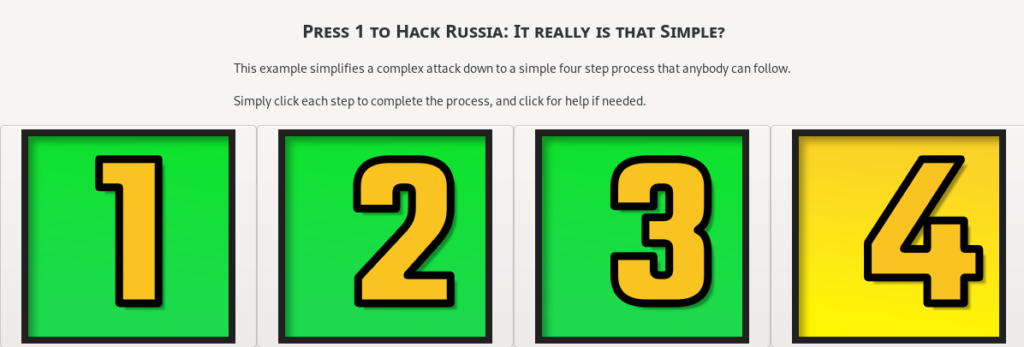
It really can be as simple as 1…2…3…4 to conduct a cyber operation anywhere in the world:
Simplified control scheme and Offensive Tools
Number based step by step interface
The core of Xorre is a custom GUI and interface that simplifies very complex technical functions into a format that can be used by anybody. Everything is built on the Qubes OS, which is the “reasonably secure Operating System” famously used by Edward Snowden.
They can access all of the required features from a simple 4 button interface that can be understood by users of all cultures or languages, regardless of technical level. All of the technical configuration is handled for the users, with no interaction required.

The software is accessed via an optimized USB hardware device, which is designed to mimic a credit or calling card. These devices are highly customizable, and can fit in an geographic region – complete with a matching “decoy app” to throw off casual investigation.
Press 1 to Start
Use at a friendly location
To start you simply plug in the device and boot it using the instructions provided (otherwise it boots into a decoy application layer) and you are presented with a simple interface. You are presented with a single clickable button, so it’s obvious where to start.
NOTE: All images are simulated using the Glade UI designer in an unmodified Fedora 35 container.
You simply click the button to initiate the process, which is pre-configured and happens automatically. This will be custom built for a particular campaign, but could do any of the following:
- Establish a secure connection with the remote server using a VPN and TOR
- Download updated packages of intelligence or offensive payloads
- Review payment information for completing an action and verify funds in a multi-signature crypto wallet – which lets you puts funds on a device, but gives control over when the money can be transferred
- Provide detailed instructions (in the local language) for the next stage of the campaign, such as where to activate the device and next steps
Once complete, simply shut down the machine and unplug the device. It uses a forensic boot so nothing is left behind.
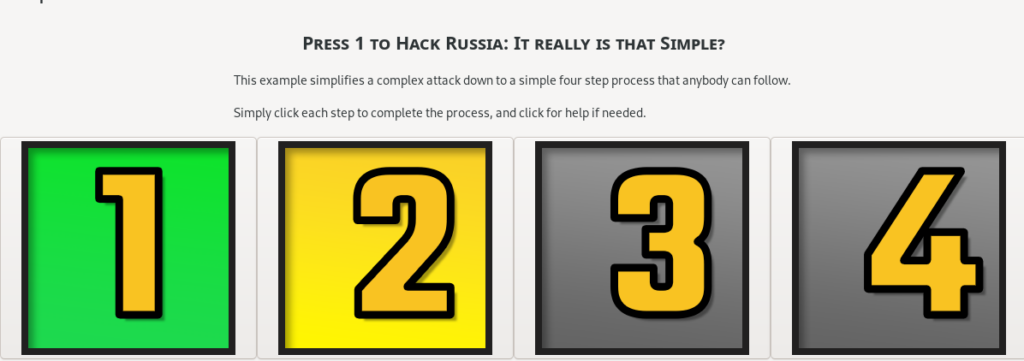
Press 2 to Initiate the Attack
Use in a hostile location
Now that the preparation is complete it is time for the operational portion of the campaign. They would take it to the desired computer or network, plug it in, boot, and follow the instructions from step 1.
The actual payload would be highly unique to each campaign, but could fall into three broad categories:
- Offensive Attack: This would unleash a purely offensive attack to steal data, wipe or encrypt drives, disrupt networks, or any false flag broadcasts
- Passive Monitoring: This would install monitoring or other intelligence gathering software on a host machine
- Establish remote access: This broadly focuses on establishing a backdoor for remote access in a system – which can be real-time (more on that later) or long-term
All of the data generated or copied (if any) will be safely stored and encrypted for you automatically. With the secure top layer decoy applications, anybody that plugs the device in without following the instructions will see only what we want them to see.
Press 3 to Finish the Attack
Use in a friendly location
Once complete, we return to our safe network and connect again.
This establishes a secure connection and transmits the data or confirmation – with the option for direct chat if needed. If everything is complete we proceed to the final confirmation and payment.
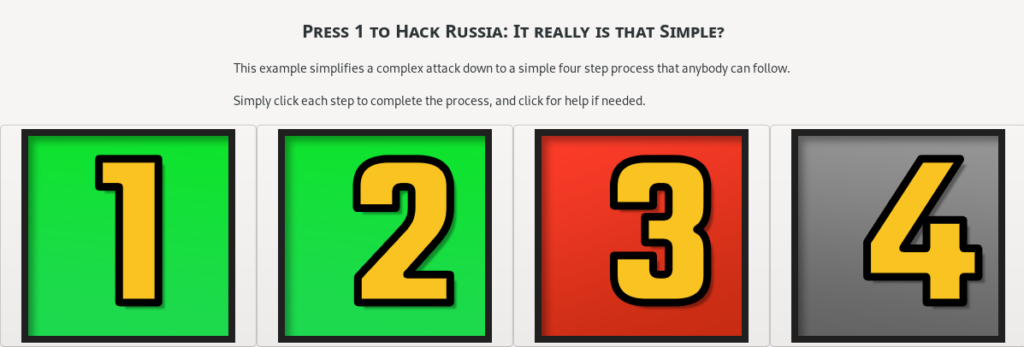
However, an operation may not complete or information may prove to be invalid. This step can be declined or rejected as needed, with the ability to specify detailed information to users if needed.
Press 4 to Get Payment
Use anywhere
Finally we are able to collect our payment, which is done with cryptocurrency. Now verified, I am able to get the other signature for the wallet which allows me to transfer funds.

I can transfer funds directly to another wallet, or generate a QR code for a local transfer.
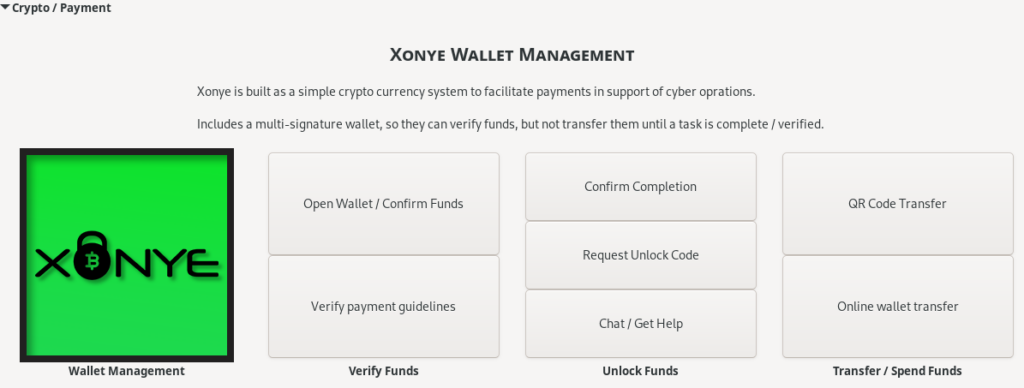
Once payment is complete and the operation is complete, the device can either be destroyed or saved for re-use.
Advanced Security Tools
These simplified control schemes can expand to the offensive security containers themselves and give users the ability to directly access relevant tools that are setup and configured to use.
Digital Honey Pots
Introducing Hazdu, one of several new offensive security containers – focused on quickly and easily creating high quality honey pots and other credential harvesting tools. These techniques have proven to be highly effective in the current global situation, and these are built using the newest tools optimized for a specific campaign.
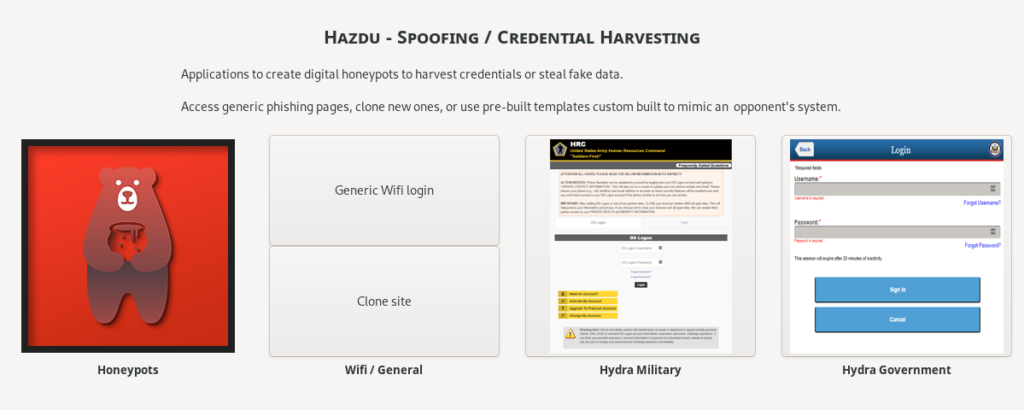
This includes the ability to create phishing or disinformation sites based on existing target systems. A user can pick from a variety of pre-built templates optimized to mirror official sources. More advanced users can also create new traps by cloning existing sites.
Offensive Security
This network security container called Kuwsi contains direct attacks on a target’s systems. This could include tools to copy, erase, or encrypt an opponent’s data.
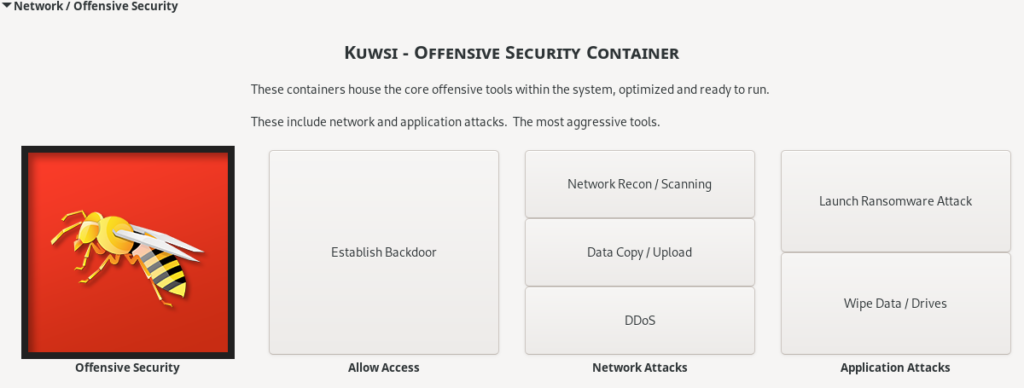
The modular nature of containers means there are an infinite combination of tools available that can be stacked in endless configurations.
Built Globally
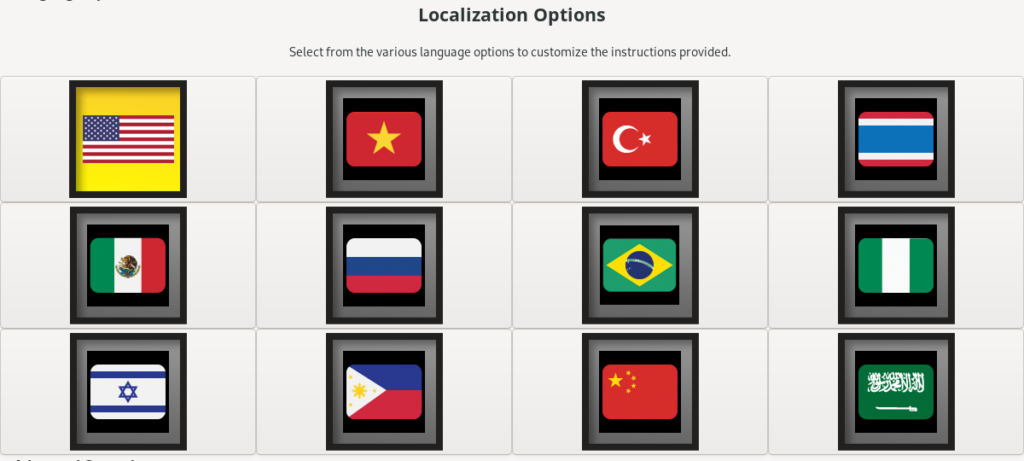
One final challenge Xorre is looking to address is the lack of localization options for many current tools – where non-English users are effectively cut off. We utilize the localization tools in Linux to create region specific versions of the tool.
Any language could be supported, but there already exist a number of localization options that are highly relevant for today’s global campaigns: